QSCIM
for Ping Identity
Our platform can streamline provisioning and deprovisioning in several identities repositories, from popular customer relationship managers (CRMs) and SaaS apps to databases and legacy applications.

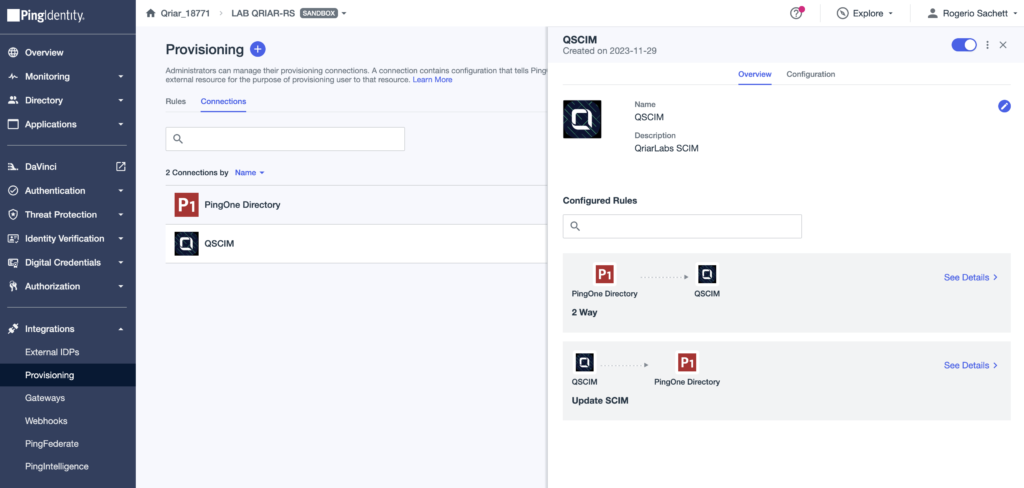
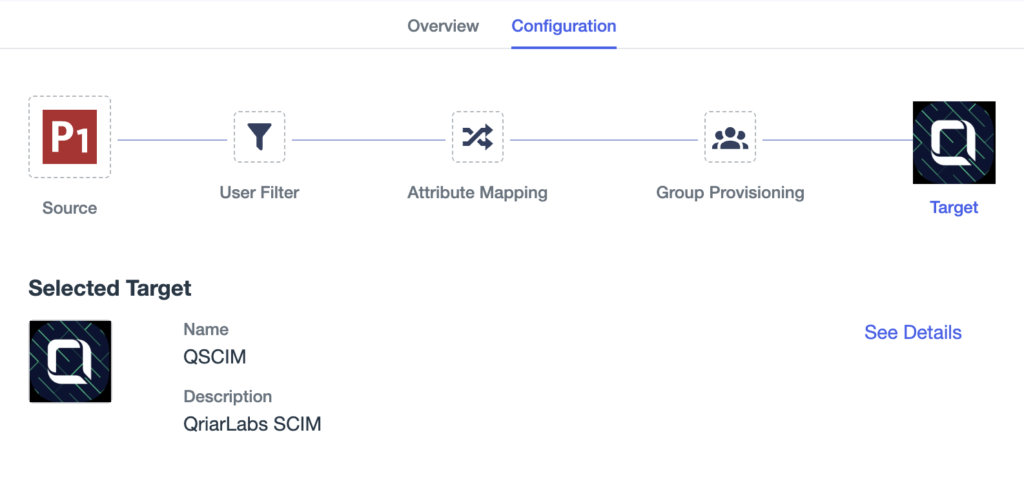
Provisioning through SCIM protocol in Ping Identity
QSCIM exposes identity repositories through REST APIs under the System for Cross-domain Identity Management (SCIM) standard. Additionally, QSCIM aggregates several key resources, such as business rules validations, third-party external APIs, data mapping, and more.
QSCIM connecting via standard SCIM Ping integration
When you create your integrations using QSCIM and then create the connections that point to QSCIM endpoints, provisioning and deprovisioning actions will automatically be integrated with your Ping environment.
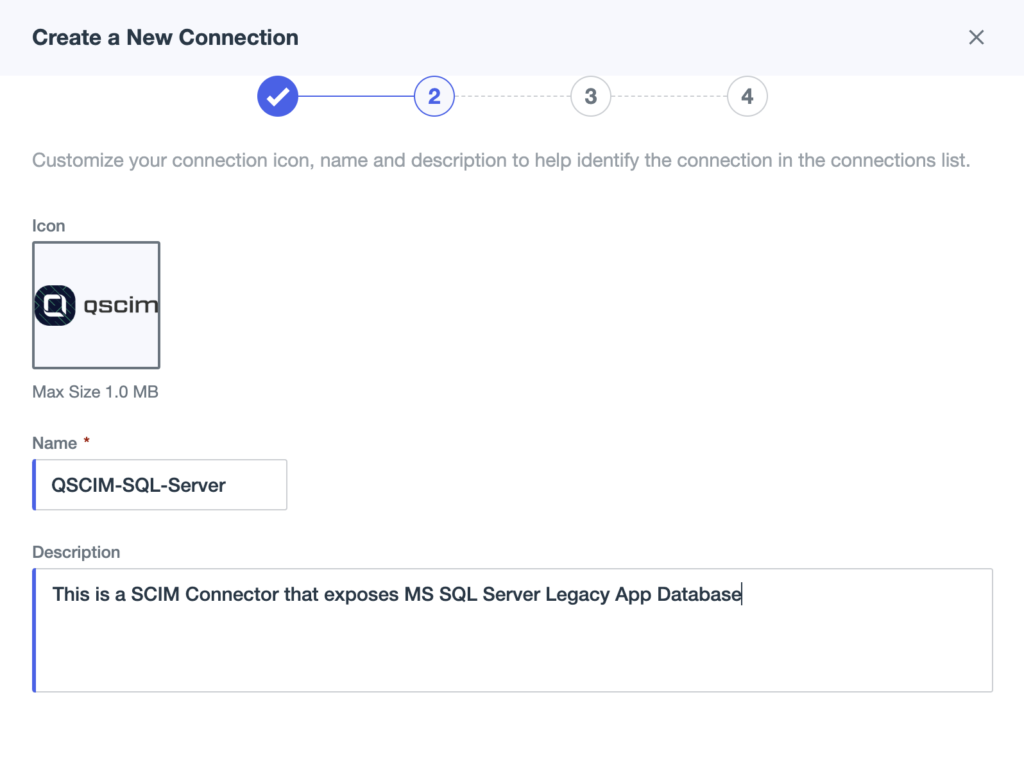
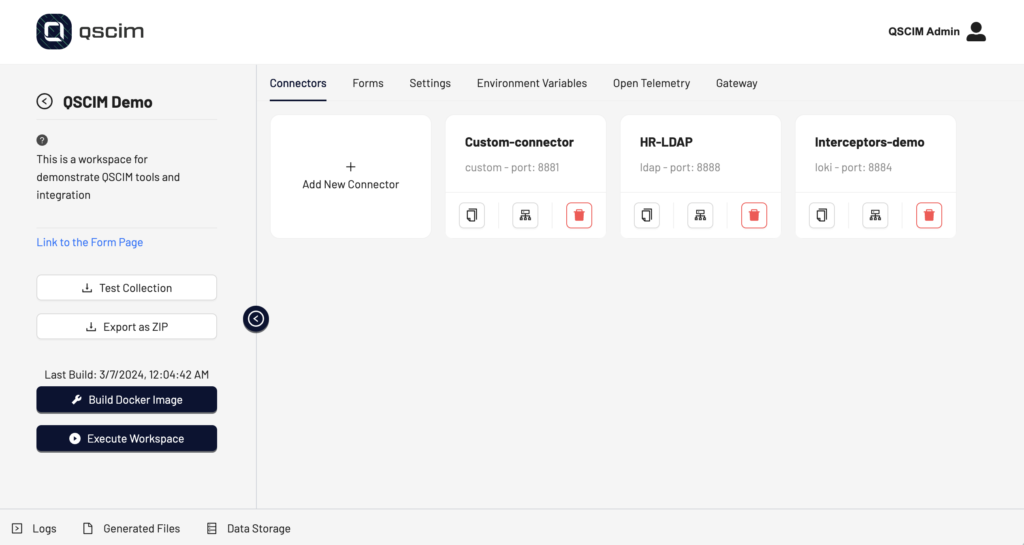
The low-code approach to enhance the user experience
QSCIM comes with several pre-established connectors while also empowering you to create your own connectors, allowing any kind of application or solution to be exposed via SCIM protocol (REST JSON API)
Top Five Reasons to Integrate QSCIM with Ping Identity
Using SCIM for provisioning and de-provisioning users in conjunction with Ping Identity, instead of relying solely on proprietary components, offers several benefits. Here are five key reasons to consider QSCIM in this context:
- Standardization and Interoperability: SCIM is an open standard designed to automate the exchange of user identity information between identity domains or IT systems. Using SCIM, organizations can ensure higher interoperability between different systems and services. This is particularly beneficial in environments where Ping Identity must integrate with other identity access management (IAM) systems, applications, or platforms supporting SCIM. Additionally, the organization avoids vendor lock-in and reduces the dependency of any solution.
- Easier Integration with Third-Party Services: Since SCIM is widely adopted and supported by numerous platforms and applications (such as SaaS), using QSCIM for user provisioning and de-provisioning simplifies the integration process with these third-party services. This reduces the need for custom development and proprietary connectors, saving time and development resources, especially using QSCIM’s low-code approach.
- Future-Proofing: Adopting standards like SCIM helps future-proof an organization’s IAM strategy. As new applications and services are introduced into the IT ecosystem, the use of a standardized protocol for identity management ensures easier and quicker integration, without being locked into a specific vendor’s proprietary approach. This flexibility can be crucial for maintaining agility and responsiveness to changing business needs.
- Reduced Complexity and Costs: By using a standardized method for provisioning and de-provisioning, organizations can streamline their identity management processes, reduce the complexity of their IAM infrastructure, and potentially lower costs related to custom integration development and maintenance. QSCIM and SCIM uniform approach simplifies the management of user identities across various platforms, leading to operational efficiencies. In migration scenarios, specially the ones where the Ping Identity is the destination, QSCIM can play a crucial role, facilitating, accelerating and reducing costs for those migrations.
- Enhanced Security and Compliance: Utilizing SCIM and QSCIM can also enhance security and compliance efforts. The standard supports consistent implementation of access control and identity management policies across different systems and services. By automating the provisioning and de-provisioning processes, organizations can minimize the risk of human error, ensure timely access revocation when necessary, and better comply with data protection regulations by ensuring that only the required information is shared and managed appropriately.
Overall, leveraging SCIM with Ping Identity for user provisioning and de-provisioning offers a strategic advantage by promoting standardization, interoperability, and efficiency, while also enhancing security and compliance measures.
Let’s chat
We would love to show you how we can help accelerate adoption or integrate with your Ping Identity
